Komplexní platforma pro penetrační testování

Seznamte se
Penterep je komplexní platforma, která jedinečným způsobem propojuje to nejlepší z manuálního a automatického testování. Její jedinečné vlastnosti maximálně zkvalitňují a zefektivňují práci. Čas, náročnost a úsilí potřebné k úspěšnému dokončení bezpečnostního testu je tak výrazně nižší než při použití jiných dostupných metod a nástrojů.
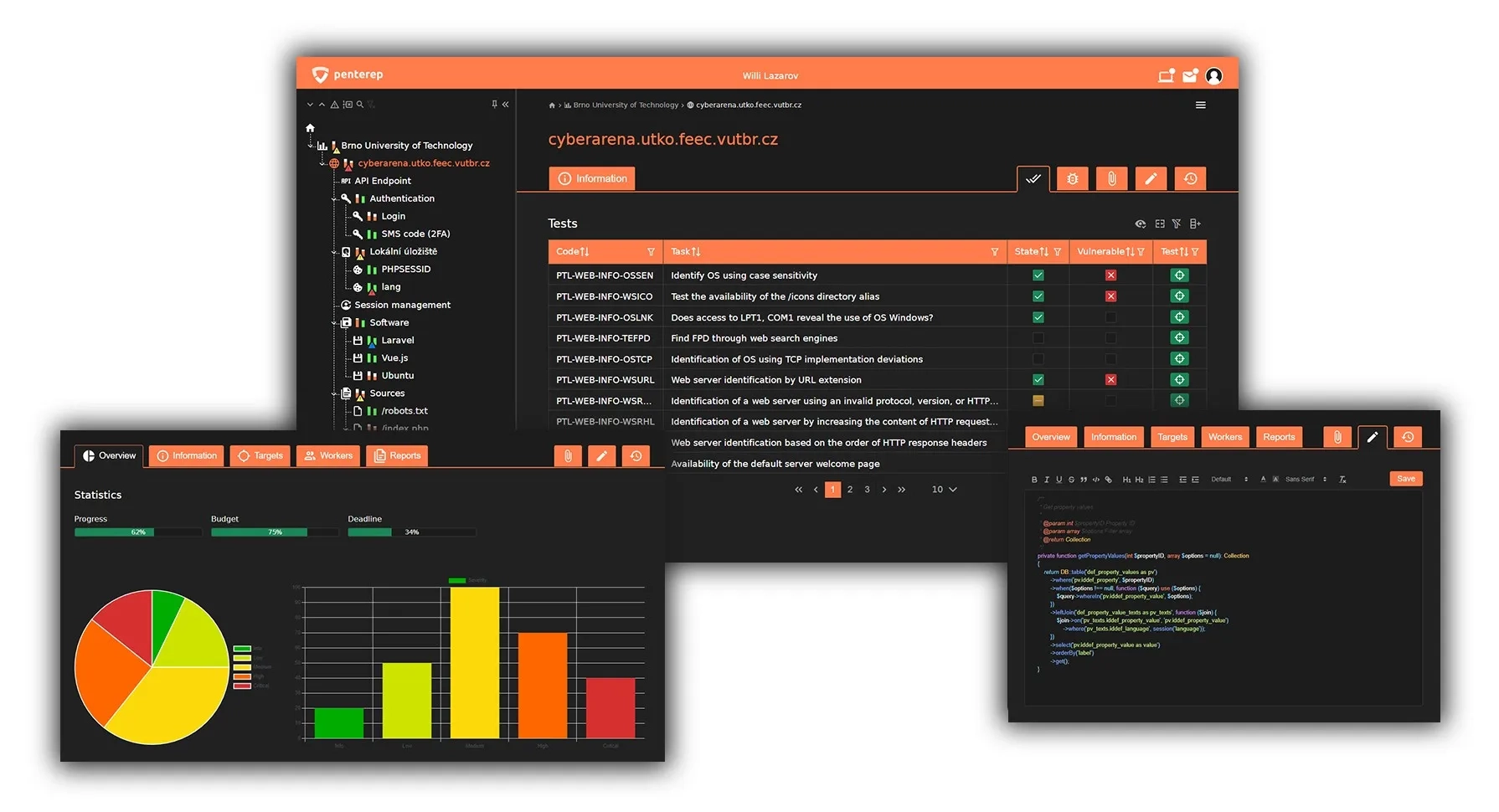
Jednou z hlavních výhod platformy Penterep je propojení automatizovaných testů s manuálním testováním. Díky tomu bude vaše práce maximálně efektivní, bude odvedena mnohem kvalitněji a dokonce i levněji. V případě automatizovaného testování by testy byly provedeny sice rychle a levně, ale bohužel pouze povrchně bez odhalení všech zranitelností. V případě manuálního testování by testy byly sice účinnější, ale současně i příliš náročné na čas a zkušenosti testera. Naše platforma slučuje to nejlepší z obou typů testování.
Platformu Penterep ocení nejen samotní penetrační testeři, ale také společnosti jejichž zaměřením je realizace penetračních testů ve větších týmech. Své uplatnění najde platforma i ve společnostech zabývajících se vývojem aplikací, nebo ve společnostech, které si sami spravují firemní infrastrukturu.
Platforma Penterep má celou řadu skvělých vlastností, které byste u jiných nástrojů hledali marně. Možnosti, které platforma nabízí, vám umožní realizovat penetrační testy v týmech, do kterých budete schopni zapojovat i méně zkušené pracovníky. Neztratíte přehled nad jednotlivými projekty ani samotnými testery a ušetříte velké množství času a peněz. Mezi vlastnostmi platformy Penterep najdete například možnost snadné úpravy checklistů, tvorbu vlastních šablon pro reporty, nebo získání reportů jediným kliknutím. Mnozí na platformě ocení také možnost intenzivního sebevzdělávání během realizace testů.
Od výrazného zefektivnění práce vás dělí už jen pár kroků
- Zaregistrujte se
- Vyzkoušejte si free verzi platformy
- Pořiďte si plnohodnotnou verzí
- Vyberte si moduly pro vaší práci
- Přizvěte pracovníky
- Začněte pracovat na projektech
Spokojení zákazníci
Co o platformě Penterep říkají ti, kteří měli možnost si jí vyzkoušet

Měl jsem možnost platformu testovat a prověřovat její účinnost při penetračních testech. Podle to co platforma nabízí se jedná o nejlepší na trhu dostupný nástroj, který pomáhá testerům s výkonem jejich činností. Kombinace manuálních kroků, které jsou vedeny léty ověřenými postupy v kombinaci s automatickými procesy je neuvěřitelně přínosná.

Jsem ve velkém očekávání. Na základě toho, jak jsem byl s platformou Penterep obeznámen a měl možnost vidět její beta verzi, jsem přesvědčen, že se jedná o zcela výjimečný nástroj. Věřím, že platforma dokáže značně usnadnit práci penetračních testerů a určitě proto vyzkouším i její plnou verzi, hned jak bude k dispozici.

Bylo pro mě velkou příležitostí seznámit se s Penterepem a jeho autory ještě před vydáním. Oceňuji unikátní přístup nástroje, který procesy testování maximálně automatizuje, ovšem přenechává testerovi 100% přehled a nevytváří falešné závěry. Snad ještě větší přínos ovšem vidím v podpoře „administrativní“ práce testera, speciálně automatizované tvorby reportu se už nemůžu dočkat!